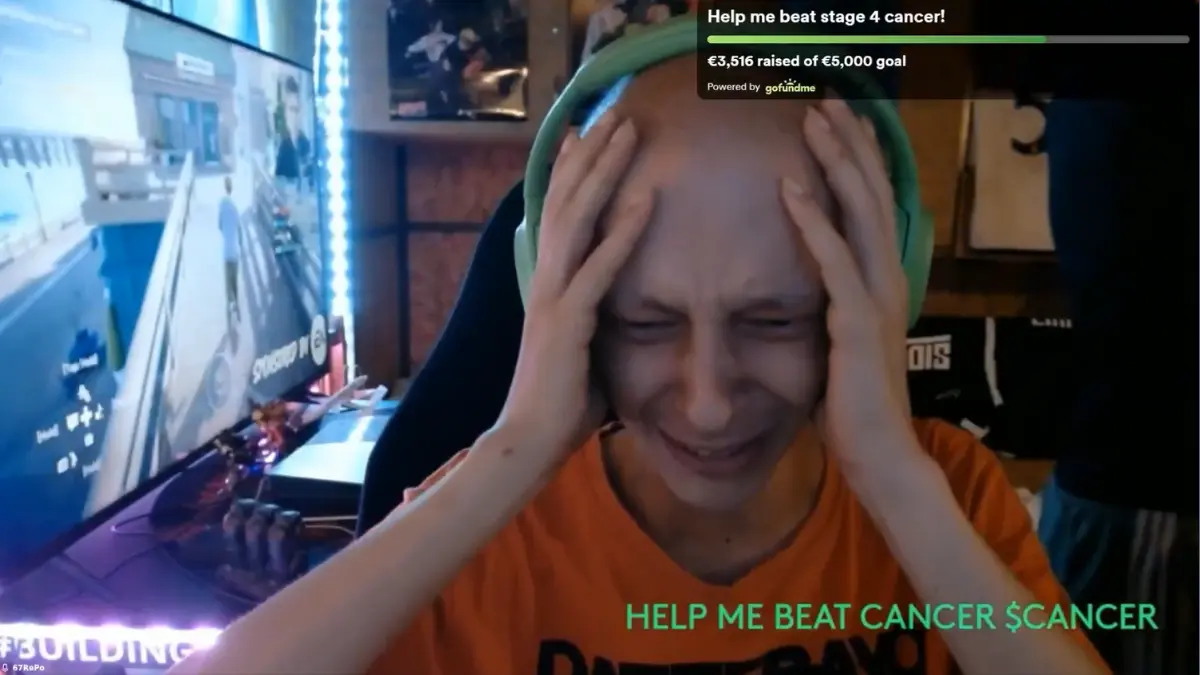
A Steam game called BlockBlasters distributed malware disguised as a regular update, leading to a devastating $30,000 theft during a live charity stream. The victim, RastalandTV, was raising money for cancer treatment when viewers suggested downloading the “verified Steam game” for their broadcast.
The malware struck in real-time. As the streamer played, approximately $30,000 in cryptocurrency assets vanished from their accounts. The theft reportedly involved assets tied to a crypto streaming platform where creators have tradable coins linked to their channels.
BlockBlasters appeared to be just another indie title on Steam’s massive catalog. The game had an official Steam page and looked legitimate enough to fool both streamers and their audiences. But behind the scenes, its developers had pushed a malicious update through Steam’s distribution system.
The fake patch contained an infostealer—malware designed to harvest sensitive data from infected computers. According to technical analyses, the malware targeted cryptocurrency wallets, browser-stored passwords, and session tokens. It even modified Windows Defender settings to avoid detection, adding its own files to the antivirus exclusion list.
Steam’s security measures failed to catch the threat before it reached players. While the platform requires two-factor authentication for developers to publish updates, this protection means nothing if the developer account itself pushes malicious code. Whether BlockBlasters‘ developers intentionally released the malware or had their account compromised remains unclear.
SteamDB, a third-party Steam tracking service, eventually flagged the game as suspicious. The warning appeared on the game’s tracking page, alerting the community to potential danger. Valve has since removed BlockBlasters from normal access on Steam, though the company hasn’t publicly explained how the malware slipped through or when exactly they took action.
This whole mess shows a big weak spot in digital game distribution. Players trust major platforms like Steam to deliver safe content. When malware arrives through official channels, it bypasses many users’ natural caution about downloading suspicious files. On the positive end, the community is rallying together, and has completely replaced the lost funds.
When your game update comes with surprise features
This isn’t Steam’s first malware incident. In 2018, a game called Abstractism was caught mining cryptocurrency on players’ computers. But BlockBlasters represents a more aggressive attack, directly stealing assets rather than just borrowing computing power. The speed and scale of the theft—$30,000 gone during a single livestream—shows how dangerous these supply chain attacks can be.
For now, anyone who recently installed or updated BlockBlasters should take immediate action. Security experts recommend disconnecting from the internet, running offline antivirus scans, checking Windows Defender exclusions, and changing all passwords. Cryptocurrency users should move assets to new wallets and revoke any active session tokens across their accounts.